Identity
Pelcro makes it easy to manage identity on the web and mobile platforms, so you can just focus on core services.
About
We provide universal authentication and authorization services for both web and mobile. Pelcro leverages state-of-the-art hashing algorithms to ensure the security of customer passwords. Below are some of the available functionalities:
- Password creation
- Update password
- Forgot password user journey (Platform & API)
- Password reset user journey (Platform & API)
Identity recipe
Click on the recipe below to see a Javascript recipe demonstrating how easy it is to use some of the identity features.
Authorization recipe
Click on the recipe below to see a Javascript recipe demonstrating how easy it is to use some of the authorization features.
Authentication Management
Pelcro uses the end user's email and password as the main authentication mechanism. Unique rules are implemented on the platform to eliminate duplicate users using the same email across the same site. Note that an account can have multiple sites associated with it.
Unique customer emails across accounts
Emails will be required to be unique across each account. If a customer tries to register twice using the same email, an error will be thrown in the registration process. If a business has multiple sites under the same account, a user created under the first site can log in to the second site using the same credentials. If a business has multiple sites that use the same top-level domain, the "auth_token" will be shared across the sub-domains and hence users will not be required to log in when navigating across the different sub-domains. If a business has multiple sites with different top-level domains, it is possible to synchronize the cookie across the domains in order to arrive at the same user experience and eliminate the need to force the user to re-login.
Unique collaborator emails across the platform
Collaborator emails are also required to be unique across our platform. This means that you can only create one Pelcro account using your email address.
Single user authentication
Single user authentication is a solution to prevent concurrent logins, which is to prevents users from staying logged into the same account from multiple places.
To disable or enable single-user authentication, you will have to follow the steps below:
- log in to your Pelcro account.
- Click on the administrator link on the top right.
- Click on settings.
- Click on "Settings" under "Site settings".
- Click on "Enable single user authentication".
SSO
Intro
Single sign-on (SSO) is an implementation that allows a user to login into different services using the same credentials. Note that how this exactly works is subject to different strategies and implementations, however, there are two main use cases for SSO:
1- Employees: SSO can be implemented for employees of a company to login to all the company's services and vendors using the same credentials. For example, Pelcro uses Gmail as our identity provider for all employees, and hence we can login using the same credentials into some of our services such as HubSpot, Mixpanel etc. This is convenient for all Pelcro employees so that they would only need to memorize a single set of Pelcro credentials.
2- Customers:: SSO can be implemented for your customers so that they can login to all of your services via unified credentials. For example, a company with services A and B would implement an SSO so the users can login into both services using the same credentials.
Let's focus on the second use case as this relates to our identity services. As an identity service, businesses can use our identity services to authenticate their users across multiple services. When you implement our Elements, SDKs, or public APIs to authenticate users, you are essentially connecting to our identity service in order to authenticate users.
How it works
When a user logins into your website using Pelcro's services, it calls on the SDK login API. Once that happens, a JSON Web Token (JWT) called "auth_token" is returned by the API which can then be used for sub-sequent APIs so that you don't have to constantly require the user to enter his credentials.
-
APIs - For users logging in using our APIs, you would need to manually pass the auth_token in subsequent API calls, the state is not maintained.
-
SDKs - For users logging in via our SDKs, we maintain the state of the user by storing the auth_token in the cookie. Note that the auth_token cookie is obfuscated however it is available via JS "window.pelcro.user.read().auth_token.
-
Elements - For users logging in via our Elements, the state is maintained as the elements uses directly our SDKs.
How to use it
1- Using our APIs: You can use our Login API reference to connect any form a user enters his credentials into, and connect it to this API to authenticate users.
2- Using our SDKs and UI Elements: You can use our SDK login functions to also connect any form a user enters their credentials into, to the SDK function. Note that this maintains the auth_token in the cookie and, as a result, we will always recognize the users if you log them using our SDK; therefore, you don't have to worry about maintaining the auth_token.
3- Using integrations: We have developed integrations to platforms such as Disqus and Milibris that leverage direct integrations, such that users can login using the same credentials into these 3rd party vendors. If you would like our help exploring such integrations, please reach out to our support.
4- Sharing the authtoken: For the ultimate SSO experience, you shouldn't be requiring the user to re-login when going from your first service to the second. When your services are across different platforms (Web vs. mobile); however, it _is possible if you have services on two different sub-domains or parts of the page. This can be done by passing the auth_token from one service to another. Once you pass the auth_token from one service to another, you can call the Customer GET API endpoint in order to retrieve this user's information.
Identity Providers/Social Logins
Pelcro allows your users to sign in to your platform using credentials from supported external social identity providers. After the user has successfully authenticated, they are returned to your platform, and their social profile information is pulled into your Pelcro directory within the meta-data.
Below, you'll find a list of the supported social identity provider platforms, along with the steps to enable them for your site:
Google
To enable the Google login/register buttons, you will have to follow the steps below:
- Create Google authorization credentials by following the steps outlined below:
a. Any application that uses OAuth 2.0 to access Google APIs must have authorization credentials that identify the application to Google's OAuth 2.0 server.
b. Go to the Credentials page.
c. Click Create credentials > OAuth client ID.
d. Select the Web application application type.
e. Name your OAuth 2.0 client and click Create
f. After configuration is complete, take note of the client ID that was created. You will need the client ID to complete the next steps. (A client secret is also created, but you need it only for server-side operations.)
g. Go to the OAuth consent screen and add the following non-sensitive scopes:
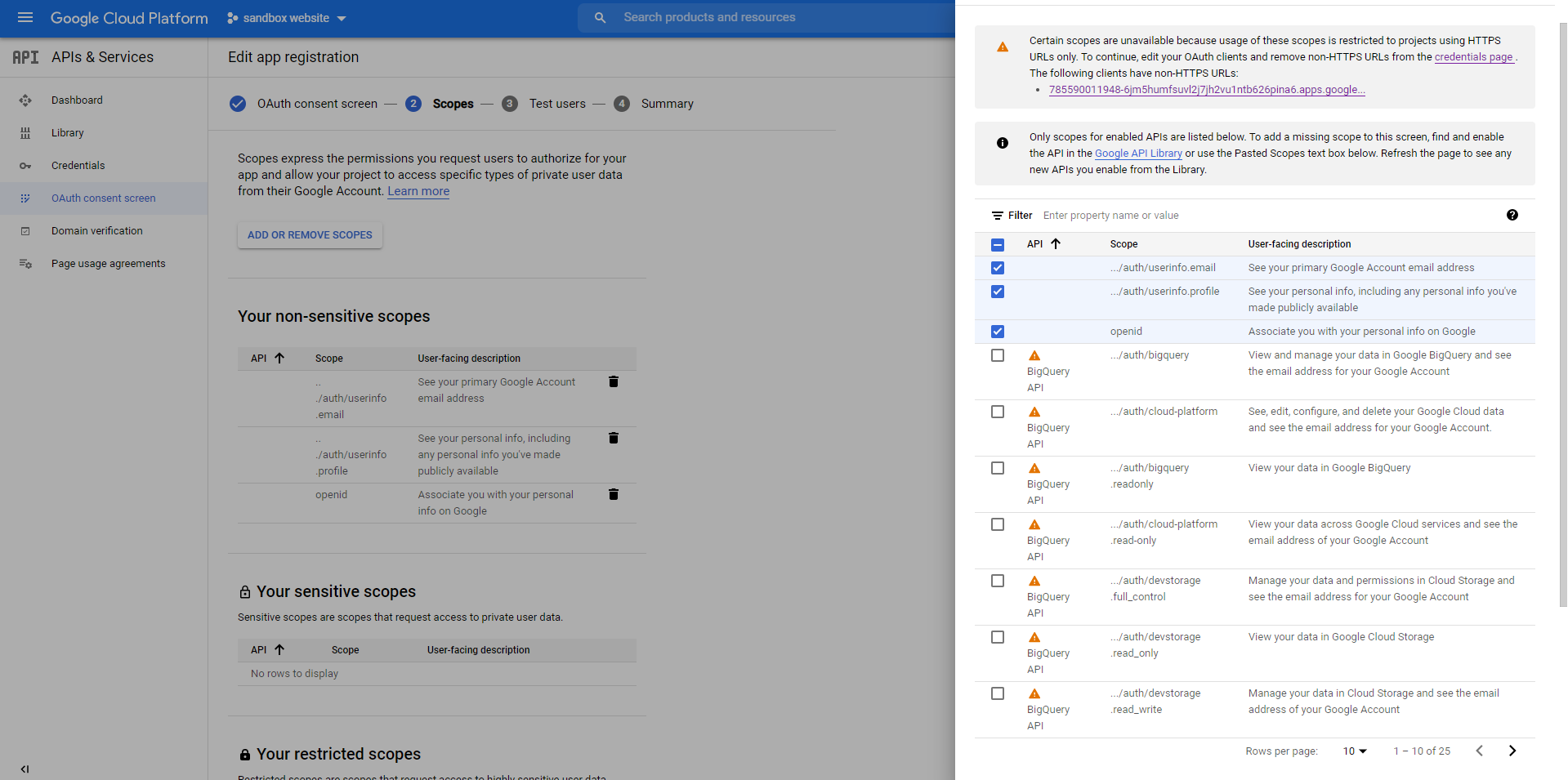
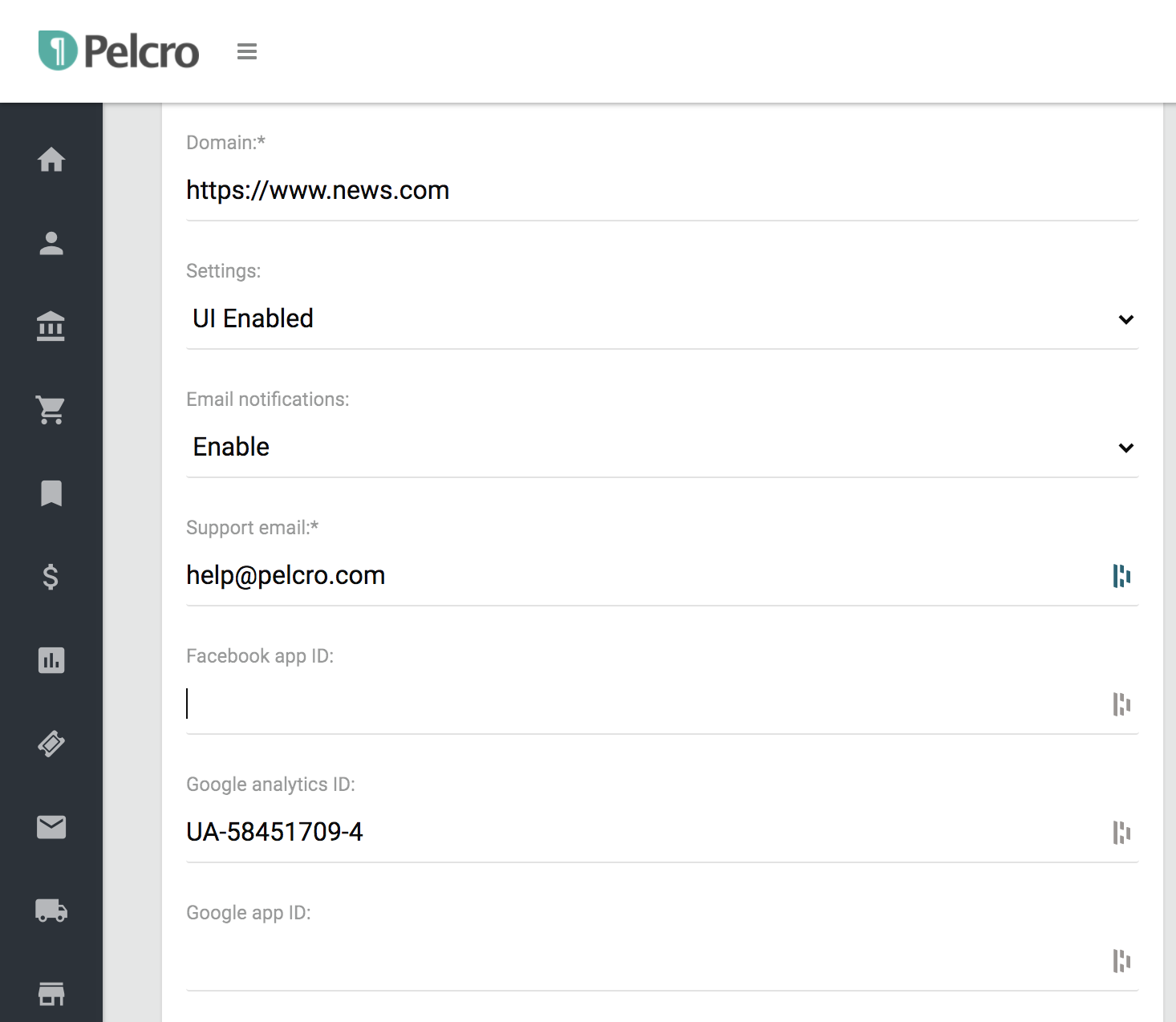
- Enter your Google client ID in "Settings" under "Site settings".
Note that, the Google login/register buttons will automatically appear if you are using the default Pelcro user interface. If the interface has been customized, you will either need to implement the buttons yourself or ask your account manager for assistance.
Facebook
To enable the Facebook login/register buttons, you will have to follow the steps below:
- Create a developer account on Facebook by clicking here.
- Register a Facebook application by clicking here.
- Enter your Facebook App ID in "Settings" under "Site settings". Note that your Facebook App needs to have completed the Data Use checkup on Facebook's side in order to be able to integrate with Pelcro's social login functionality. For more information please check this page
Note that, the Facebook login/register buttons will automatically appear if you are using the default Pelcro user interface. If the interface has been customized, you will either need to implement the buttons yourself or ask your account manager for assistance.
Auth0
Using Auth0 means that you will let Auth0 manage the authentication process in the same way that Google, Facebook, and any other Identity provider redirects to their server whenever a user signs in.
To enable the Auth0 login/register buttons, you will have to follow the steps below:
- Create an Auth0 account by following the sign up steps on their page
- You will need to create an Auth0 application. Pelcro IDP supports Auth0 regular web applications. When you create an application in the Auth0 Dashboard, Auth0 assigns it a client ID which is an alphanumeric string that is the unique identifier for your application. You will use this ID in your application code when you call Auth0 APIs.
- Follow the steps to create an Auth0 application. You will need to register a regular web application.
- After completing the application creation flow, you will need to navigate to the Application sections from the sidebar on your Auth0 Dashboard.
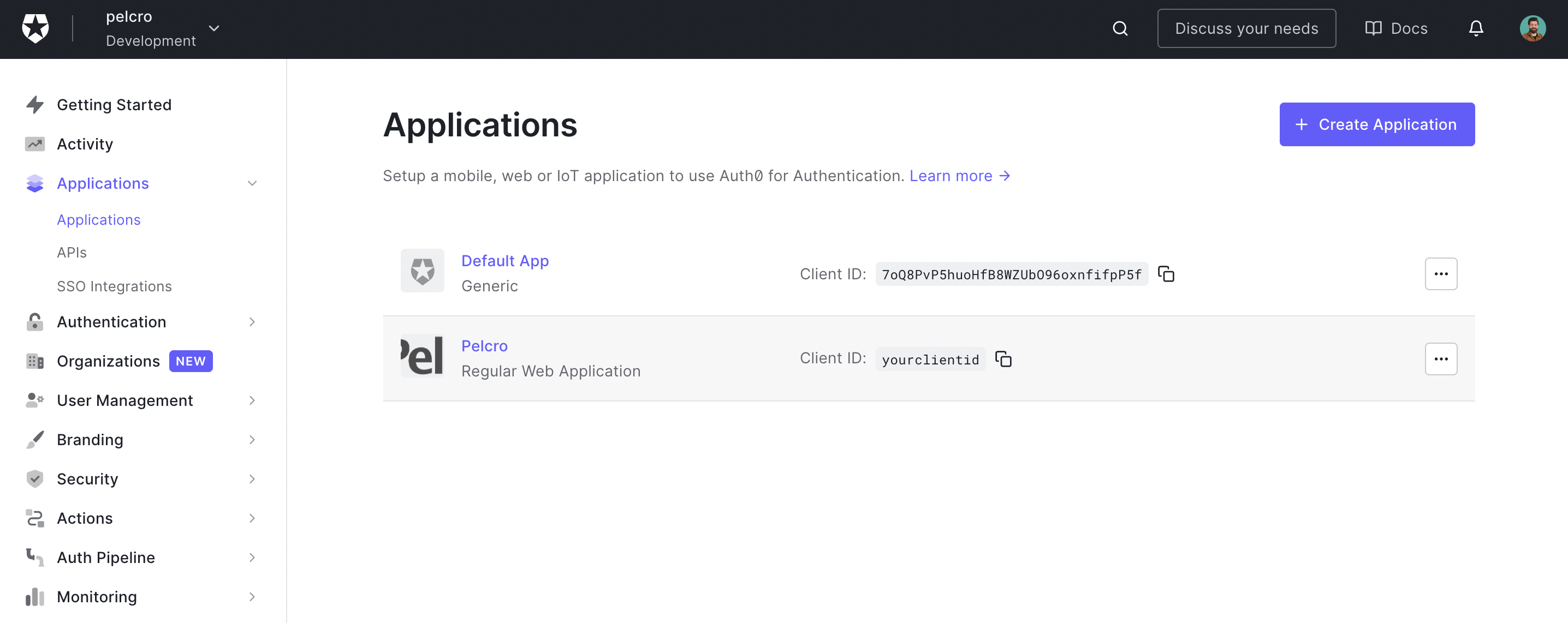
- Click on the application you created, or alternatively, click on the ellipsis menu and choose settings to go to your application settings, which will open the screen below. You will need to copy the following information:
a. Client ID
b. Domain
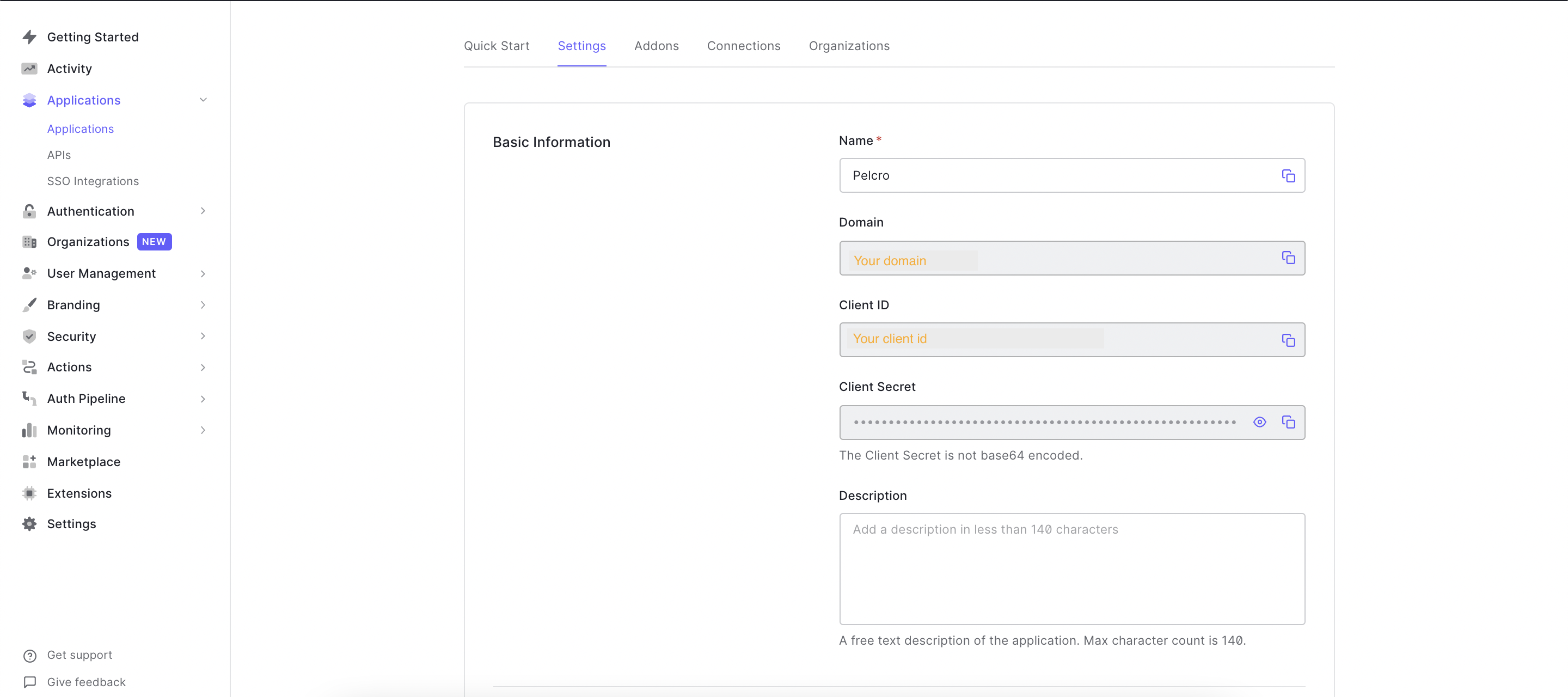
- You'll need to fill out the following fields:
a. Under "Allowed Callback URLs", add your fully qualified domain name (e.g. https://yourwebsitename.com)
b. Under "Allowed Web Origins", add your fully qualified domain name (e.g. https://yourwebsitename.com)
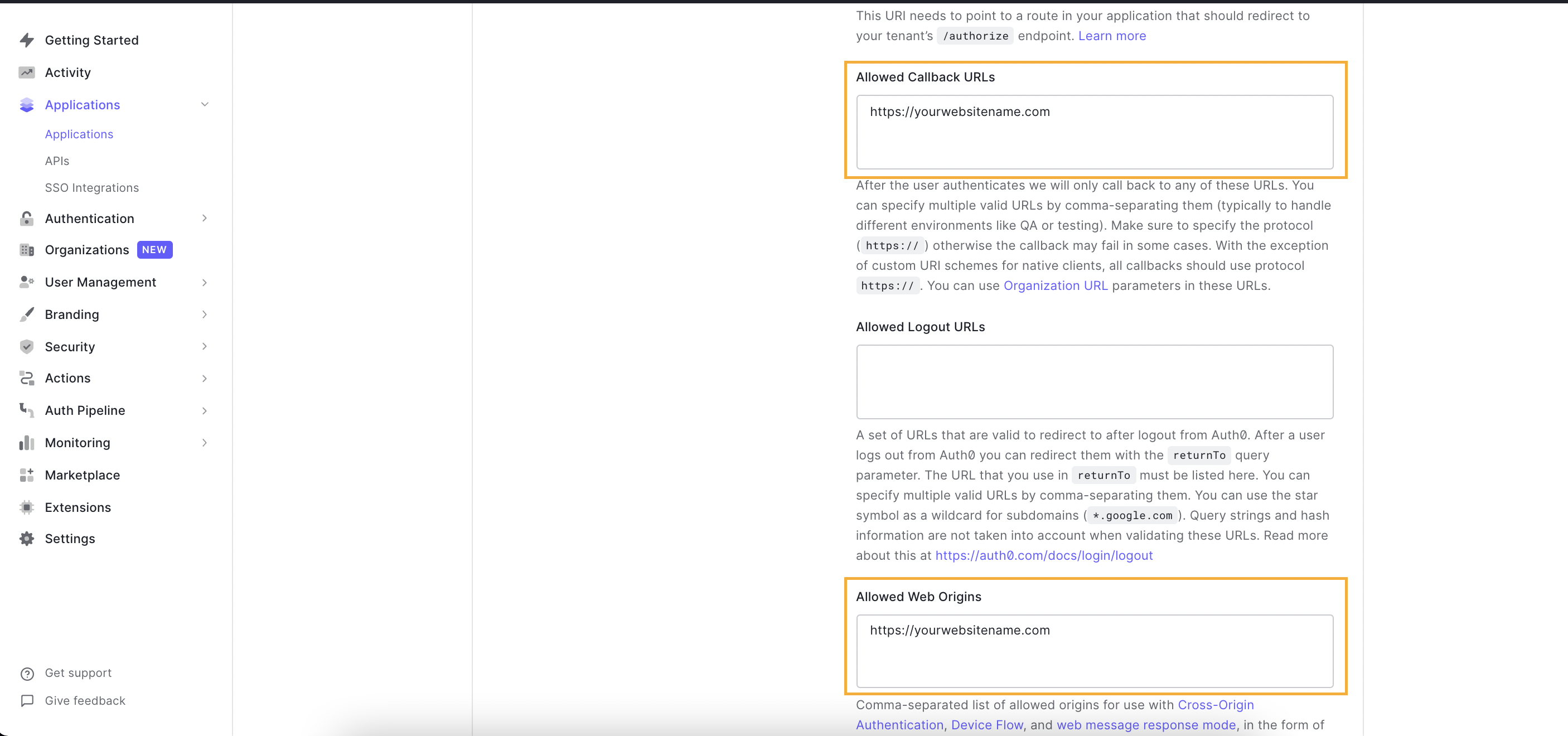
- Finally, Enter your Auth0 Client ID and Domain in the Pelcro settings page [here] (https://pelcro.com/admin/settings).
Note that, the Auth0 login/register buttons will automatically appear if you are using the default Pelcro user interface. If the interface has been customized, you will either need to implement the buttons yourself or ask your account manager for assistance.
For more information about our social login functionality, please refer to the below documentation links:
- Pelcro's JavaScript SDK
- Pelcro's SDK API
- Pelcro's Elements
Updated 5 months ago
